This time we try to discuss about aplication exploitation with SEH and SafeSEH. One of the aplications that use SEH protection is BigAnt, so we can use it to try on our LAB. As usual as before, we must prepare our tools there are :
1. Ollydbg
2. Python
3. Bigant
4. LAB (Win XP SP3)
No we come to the steps...
1. Prepare on LAB
Run BigAnt Server on our LAB and also run Ollydbg, then attach AntServer process.
2. Fuzzing
Create a fuzzer using python language, in this case we can use "USV " command owned by BigAnt Server.
here are the codes :
#!/usr/bin/python
import socket
target_address="192.168.56.101"
target_port=6660
buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
import socket
target_address="192.168.56.101"
target_port=6660
buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
the codes means we sent 2500 byte buffer to BigAnt Server that use port:6660. Then run it, and we can see the result on Ollydbg
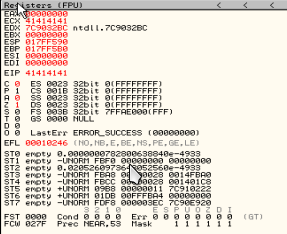
picture above showed us how BigAnt crashe, but EIP register not overwrited, its happen because BigAnt use SEH. If we want to know the error we can view SEH chain
to continue data from SEH chain into memory we can press Shift+F9.
now we can see EIP register overwrited by 0x41414141.
3. Pop, Pop, Retn method
Explanation about POP,POP,RETN method and why we use that method can we read from a book named "Harmless Hacking" by our lecturer Mr. MRP. in this post we dont discuss it and we can through it.
Next, using third party dll file name vbajet32.dll as a springboard to overwrite SEH protection. We can find POP,POP,RETN command from vbajet32.dll module in the ollydbg.
From Ollydbg -> View -> Execute Modules -> attach vbajet32.dll process. Next Right click on the mouse and search for -> sequence of commands -> write POP r32,POP r32, RETN. Finally we can see the address of vbajet32.dll
4. Create and Offset pattern
Same as step to exploit WarFTP, the next step is creating pattern and copy the pattern to the fuzzer and then run the fuzzer
now we know how much bytes data we must sent into target from the result of the offset.
Next step, still on the same fuzzer we make change on it like this :
then run the fuzzer again. The result should be BigAnt crashed and access violation on memory occured that we can see in SEH handler.
5. CPU process controll
After we get the address byte to drag out SEH, now its time to put address of vbajet32.dll who have command POP, POP RETN into fuzzer. the codes look like,
Restart Ollydbg dan BigAnt server, put a breakpoint into 0F9A196A memory address inside vbajet32.dll module. After it run the fuzzer.
Now we can see from SEH handler this change,
To direct the CPU process from 4 bytes into the empty space, followed by the command SEH overwrite address, we can use JMP SHORT command.So we can write 6 byte opcode value into fuzzer, and its the change come ike this:
6. Generate sheelcode
We can use msfweb as like as way to exploit warftp, the most important things is we must pay attention to "BAD characters" ,i will post the way to find Bad char in different post.
Next, we can copy the codes generated by the payload and add 16 byte nop padding before the codes to the fuzzer.
The last step is run the fuzzer on target and then try to connect to the system.
Finally done...










Tidak ada komentar:
Posting Komentar